How to select the best Cloud Access Security Broker for your organization
Cloud Access Security Broker (CASB) is a solution that packages essential cloud ecosystem security features: visibility, data security, threat protection, and compliance. There are many CASB providers, so you need to understand what kind of cloud services you are looking to protect and think about use cases so that you can select the best CASB for your organization.
What is a Cloud Access Security Broker?
Cloud Access Security Broker (CASB) is a solution that packages essential cloud ecosystem security features: visibility, data security, threat protection, and compliance. These features are described in more detail in the picture below.
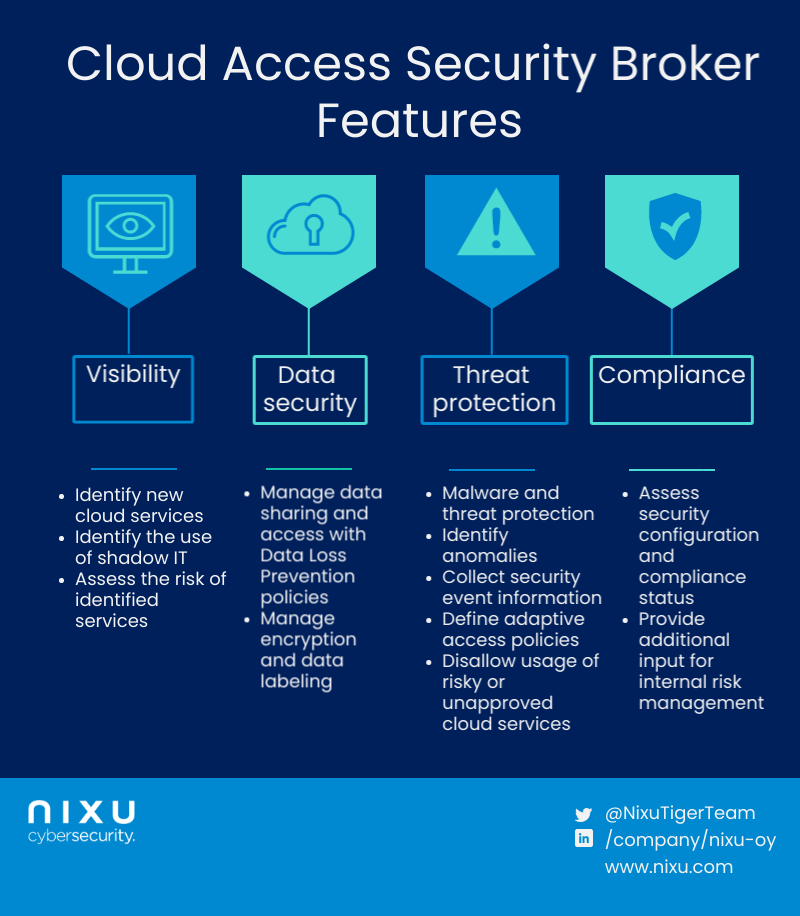
Visibility features help you to identify new cloud services used by your organization.
Data security features help you in managing the sharing of data with Data Loss Prevention (DLP) policies, encryption, and labeling.
Threat protection features help you to identify malware, attack attempts, and other incidents and collect security event information for a Security Operations Center (SOC).
Compliance features allow you to assess SaaS and IaaS against regulations or standards and provide input for your risk management processes.
Same features, different approaches
Under the four pillars of CASB, there is room for different approaches. While most solutions aim to provide capabilities to address all of the four domains, there are differences in the features as well as technology choices.
API-based features have generally provided better access and control to the cloud platform or the service. These are a useful way to monitor already identified and allowed services.
Proxy-based implementations can monitor the traffic in and out of cloud services and cover unsanctioned services and provide, e.g., malware scanning, usage analytics, and improve dynamic access control.
Some solutions can also include agent software installed on the end-user devices. These agents provide features like redirecting the user to utilize services allowed by the organization when the user attempts to use unsanctioned cloud service. Agents can also offer, depending on the vendor's background, other features like more fine-grained control on confidential material and better visibility to service usage.
Practically all CASB solutions include both API and proxy-based features to some degree. While one approach can be more effective than the other (i.e., API vs. proxy-based), there are often pros and cons in each method.
Cloud access security brokers are a fast-developing market, which can make it hard to navigate when trying to select the most suitable solution for your ecosystem. In most cases, it's a good idea to compare and evaluate several different solutions to make sure they fit your needs. The key questions you should consider are:
- What cloud services or platforms we have, and how do we use them?
- What are we worried about in our cloud ecosystem?
- Should I stick with a familiar vendor?
Read on to learn more about these topics.
What do we have, and how do we use it?
First, you should identify what kind of cloud services or cloud platforms you are looking to protect. Does the vendor provide integration for those?
Although one of the CASB features is to identify unknown cloud services within organizations, the best and perhaps obvious starting point is to list what cloud services you are currently using. While platforms, like Microsoft Azure, Google Cloud Computing Platform, and AWS are the easiest marks on the list, you should attempt to list as many cloud services as you can.
You should also think about your priorities in protecting those services. What are the crown jewels of your cloud ecosystem? What's critical?
What are we worried about in our cloud ecosystem?
After determining what we have and what we need to protect, the next step is to define our concerns. What kind of threats are we facing? What services include confidential data? What services need to be accessed securely using an airport or cafeteria Wi-Fi?
Examples of concerns:
- We don't know whether our cloud services are compliant with obligatory regulations or standards.
- Users access our services from around the world. We can't determine in real-time whether the access is legitimate.
- We don't have consistent security monitoring in our cloud services.
- Users use alternative unsanctioned cloud services to which we have no visibility.
For each of the identified concerns, we can define a use case. To write a use case, consider, for example, what are the worries you are thinking to address with CASB, who will be operating it, and who are interested in the result. Here's a list of use-cases based on the examples above:
- Determine the compliance status of a cloud-platform X against regulatory requirement framework Y.
- Ensure secure global user access to cloud services. Define rules describing when, from where, and to what to grant access.
- Integrate CASB to SIEM operated by a partner, to provide input for security monitoring.
- Gain visibility to the unsanctioned cloud services the users are using with company-provided devices.
Remember the project management triangle? You can only get two out of good, cheap, and fast. Similarly, in CASBs, you might need to find a balance between visibility, data security, threat protection, and compliance. You should prioritize your use cases and cloud services. Many CASBs are modular, and a phased implementation will probably be more cost-efficient.
Many vendors offer public Request for Information or Request for Proposal templates. A simple search for "CASB RFP template" can reveal valuable insights about what to consider in your use cases and what features to ask for from the vendors.
Should I stick with a familiar vendor?
Some vendors have built CASB capabilities to supplement their own cloud ecosystem, or otherwise heavily emphasize particular technology stack support. They may provide better synergy with certain cloud technologies. These "ecosystem specific" CASB solutions are definitely worth the evaluation. For example, Microsoft Azure benefits from MCAS, while a network environment with Palo Alto devices integrates well with Prisma SaaS features.
In some cases, a familiar vendor can be deemed the best alternative with a considerably less effort compared to full-blown RFI/RFP.
However, you shouldn't neglect the evaluation of more generic solutions. If you have a considerable amount of SaaS in use outside of the vendor's ecosystem, or the platform only caters a part of your organization's needs, and you might need to expand later, the CASB might not fit all your needs after a while. In most cases, you should evaluate at least a couple of vendors.
Dos and Don'ts of selecting a CASB
As a summary, here are some DOs and DON'Ts we have considered as useful guidelines after evaluating various CASB solutions.
DO
- Define what cloud services and platforms you have
- Try to define use cases, i.e., a simple list of statements describing what you are looking to utilize the CASB for.
- Ask for the vendor's development roadmap for the solution to see what's ahead.
- Ask for references, preferably for the same type of organization you are managing. Check the references and ask about their experiences.
- Perform a proof-of-concept / proof-of-value, with the selected vendors.
DON'T
- Rely too much on public material, vendor datasheets or marketing material, or other evaluations older than one year. The fast-developing market has most likely made these obsolete.
- Rely on recommendations only. Performing RFI, even with one vendor, is, in most cases, the best way to ensure that the solution fits your needs.
Want to keep track of what's happening in cybersecurity? Sign up for Nixu Newsletter.

